Use Cases
Network device configuration backup
Netpicker can automate the process of backing up configurations from 150+ vendors of network devices. It can be configured to periodically check and save the latest configurations, ensuring that there’s always an up-to-date backup available. This is crucial for disaster recovery and maintaining network stability.

Network compliance
Compliance checks can be automated using Netpicker. It can use pytest (python unit testing framework) to verify if the network configurations adhere to specific standards (such as CIS) or internal policies. This includes checking for proper configurations, ensuring no unauthorized changes have been made, and maintaining consistency across the network.
CIS hardening
The Center for Internet Security (CIS) provides benchmarks for secure system configuration. Netpicker can be used to ensure network devices are configured in line with CIS benchmarks, helping to harden the network against vulnerabilities.
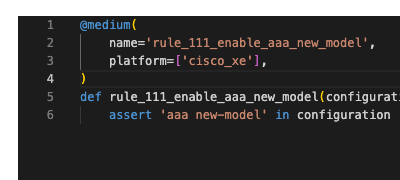
CVE vulnerability assessment
Netpicker can assess network configurations for vulnerabilities listed in the Common Vulnerabilities and Exposures (CVE) database. It can automatically check for configurations that are known to be vulnerable and suggest necessary updates or patches.
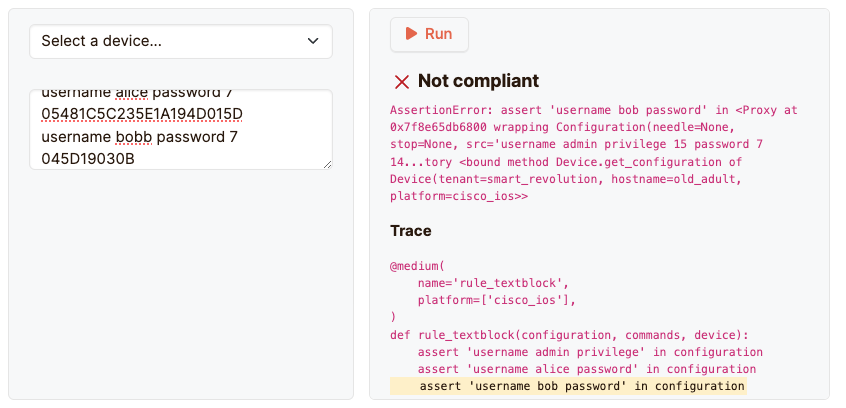
Network design validation
Before deploying new network designs, Netpicker can validate the configurations against the planned design. This helps in ensuring that the network is set up as intended and meets all the design requirements.
Multi-vendor, multi-node validation
Netpicker’s versatility allows it to work across different brands and types of network devices. This is essential in multi-vendor environments where consistency and compliance need to be maintained across various devices from different manufacturers.
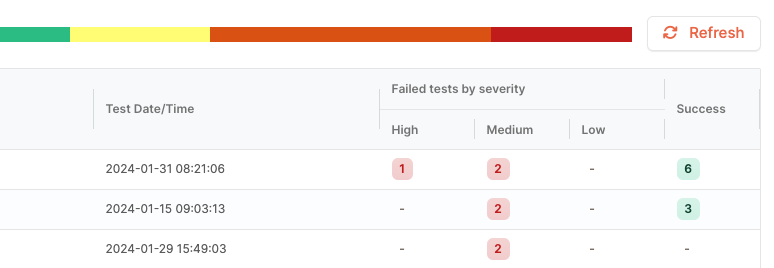
Network security assessment
By analyzing network device configurations, Netpicker can identify potential security weaknesses. It can assess the configurations against known best practices for network security, alerting engineers to any settings that might make the network vulnerable to attacks.
Any question?
Ask us anything. About pricing, to get a quote, a specific setup or any other requirement?
Contact our sales team for help
